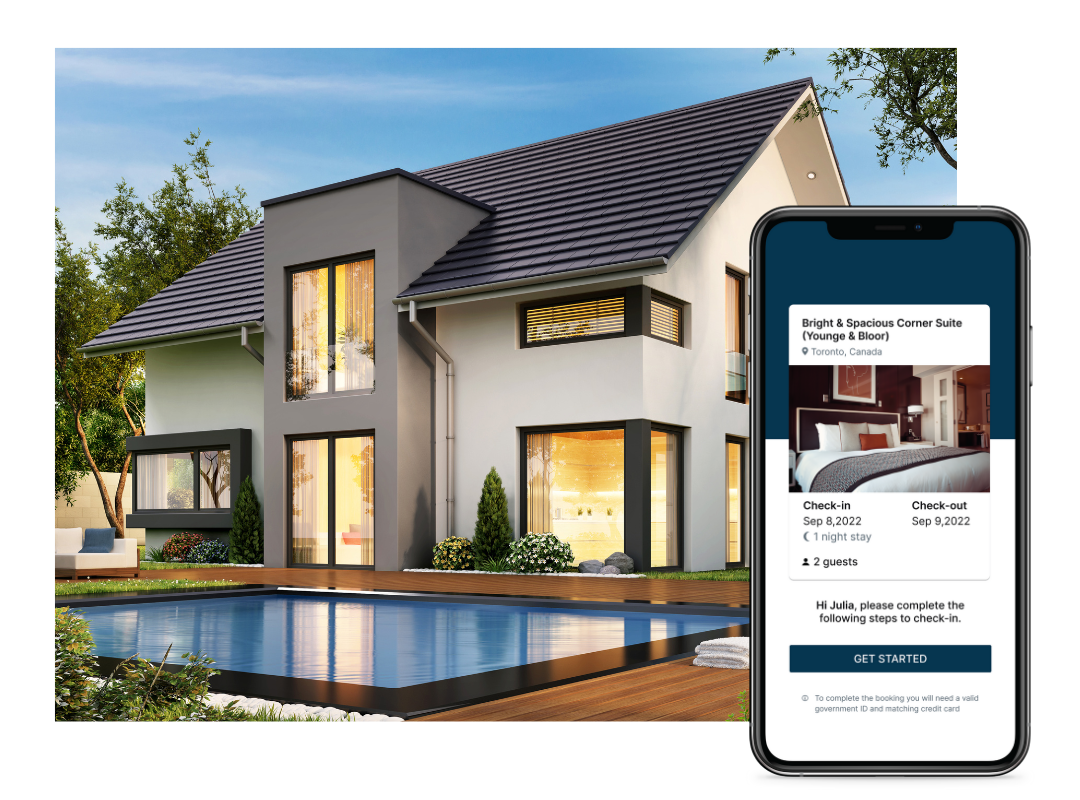
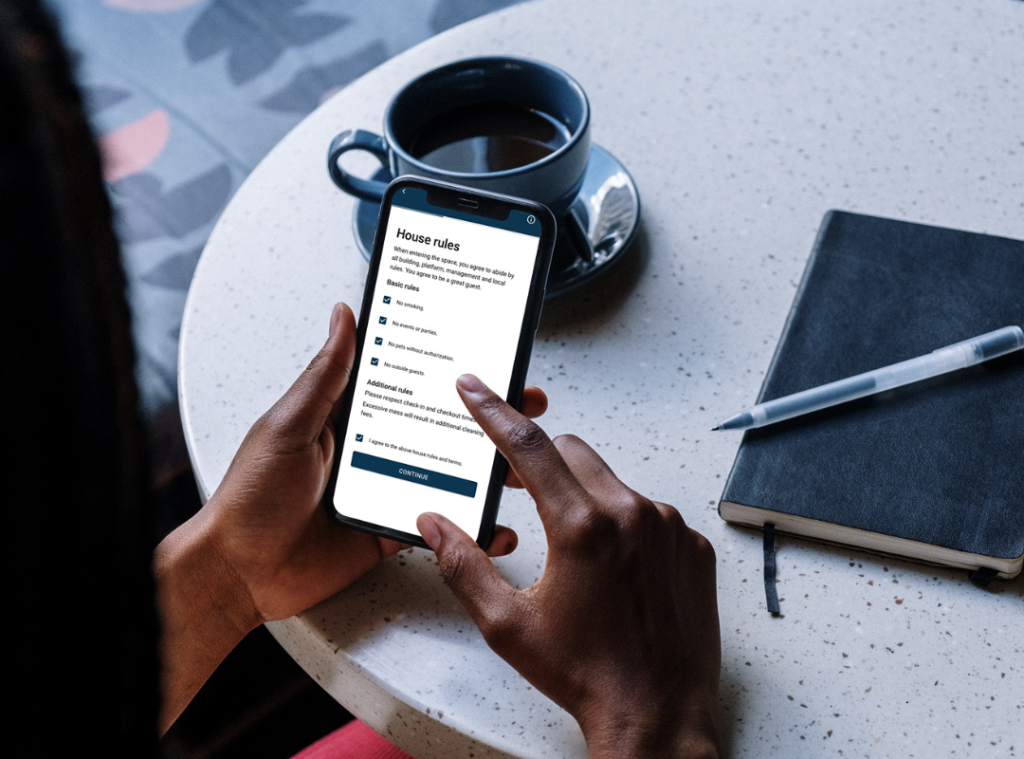
A rise in fraudulent activity caused by the pandemic has cemented the fact that property managers can’t rent their properties out to just anyone. That’s how you get hit by parties, property damage and criminal activity. To prevent these types of incidents, property managers rely on security measures to vet their guests ahead of time.
One of the most common security measures is ID verification, which involves confirming that the personal information submitted by the guest corresponds with their real identity. While the end goal is the same, different companies approach the ID verification process in different ways. Larger property management companies may rely on third-party vendors to automate the process, while smaller property management companies may opt to do it manually—collecting and reviewing ID documents for every guest.
KYC in hospitality:
In the banking and finance sectors, KYC is a standard practice used to verify the identity of an individual or a business entity. In the hospitality context, KYC encompasses not just ID verification but a full spectrum of analyses—think of it as deep-diving into multiple pools of data to get a 360-degree view of your guest. It can include scrutinizing transaction history, social media activities, behavioral patterns, and even travel history to evaluate the potential risk of illegal intentions.

How Does It Work?
Imagine you’ve got a guest who’s passed the ID verification checks, but there are a few red flags in the reservation details—maybe it’s a last-minute booking for a single night, and the guest is local. Traditional ID verification may let this reservation slide through, but KYC will urge you to take a second look.
The KYC process will typically involve:
Document Verification: The initial step, similar to traditional ID verification.
Behavioral Analysis: Scrutinizing the guest’s actions during the booking process, like the speed of filling forms or the device used for booking.
Transaction Monitoring: Looking at the method of payment to see if it aligns with typical guest behavior or flags as unusual.
Social Media and Online Presence: Evaluating the guest’s digital footprint for congruency with their given “story.”
Previous Stays and Reviews: Checking feedback from other property managers or hotels where the guest has stayed before.
The role of ID verification in rentals can be explored further in articles about streamlining security in the hospitality industry.
Why It’s Crucial?
KYC allows you to create a comprehensive risk profile that can inform your decision-making process more effectively than just an ID verification. It acts as a complementary tool that fortifies your vetting procedure, giving you the confidence that you’ve done everything you can to ensure the safety and integrity of your property.
And let’s face it, while a fraudulent guest might go through great lengths to forge an ID or even provide a stolen one, it’s significantly harder for them to fabricate a convincing digital life or consistent behavioral patterns. In other words, the more layers of verification, the harder it is for fraudsters to slip through the cracks.
So, while ID verification remains a critical aspect of guest vetting, incorporating KYC into your hospitality business can make your preventive measures more robust. With the rise of increasingly sophisticated fraudulent tactics, it’s more important than ever to cover all your bases. Because when it comes to the security of your property and peace of mind, there’s no such thing as being too careful.
ID Verification and Background check:
Proper ID verification is a great first line of defense when it comes to preventing malicious incidents. But unfortunately, fraudsters are becoming more sophisticated, outmaneuvering current ID verification methods. This means that even property managers with the most thorough process can still be left exposed to fraud, parties and worse.
Debating the sufficiency of ID verification is linked to how security is streamlined in hotels.
How ID verification works?
There are multiple methods used to verify a person’s identity. They can range from verifying a guest’s personal information online to examining their physical IDs to using cell phones to confirm their identity. The process used will depend on the transaction and the level of risk associated with it.

In the case of short-term rentals, the risk level tends to be higher since you’re giving a stranger access to a major asset: your property. As a result, the short-term rental ID verification process should require the guest to submit a copy of their government-issued ID. Then it’s up to you as the property manager—or the vendor you’re using—to check the information on the ID against the booking information, ensuring it matches.
To confirm that the ID hasn’t been tampered with, you can use ID parsing technology to scan the document, checking whether there’s information encoded in the barcode on the back of the ID, and if that encoded information matches the information on the front of the ID.
To protect against stolen identities and impersonations, you can collect selfies and match the guest’s face to the photo on the ID document.
Related Post: How Does Vrbo ID Verification Work? The Complete Guide
Where ID verification falls short?
There’s no denying it—ID verification is an important part of any hospitality business as it helps remove anonymity from the guest’s reservation. By implementing the right tool, you can flag attempts to evade identification or deceive your guest services team.
For example, oftentimes when someone modifies information on their ID, they mess with the document’s security features, so by examining these, you can see if a guest is using a digitally-altered ID.
On the other hand, if a guest is using a stolen ID, you can catch them with facial recognition technology by matching their selfie with the photo in the ID they provided.
Requiring the guest to upload a photo of themselves creates an extra hurdle that might deter a fraudster, but it still can’t verify your guests with 100% certainty. These days, selfies, and other personal details, are available through darknet forums and marketplaces. Fraudsters can purchase legitimate user profiles, containing a real ID and other information they need to fool a basic identity check.
In the mix with legitimate (but stolen) IDs are professionally forged documents. Modern counterfeit IDs have become so advanced that they can go undetected by ID verification solutions, especially when the barcode information matches the information on the front of the ID.
The limitations of ID verification highlight the importance of understanding Vrbo’s ID verification process.
Booking.com id verification:
When we discuss ID verification and KYC in the hospitality industry, it’s worth noting platforms like Booking.com have implemented some advanced verification features. Their ID verification process typically includes requirements for government-issued IDs and often features real-time verification, which not only adds an extra layer of security but also complements the KYC procedures you may already have in place.
As a host, you receive a wide array of information about your prospective guest, ranging from past stay reviews to booking behavior. This data is invaluable for creating a more comprehensive risk profile of your guest, as encouraged by KYC practices. By leveraging the resources provided by Booking.com’s ID verification system, you can bolster your existing KYC measures, creating a more resilient and comprehensive guest-vetting procedure.
While it may be tempting to rely on third-party platforms like Booking.com to handle all aspects of ID verification, remember that these systems are most effective when used in conjunction with your own guest screening methods.
ID verification is not foolproof.
To keep up with the increasing sophistication of cybercrime and fake IDs, you need to be looking at other data points as well—not just the ID document.
Leveraging alternative data
To prevent all types of incidents at your properties, you need to analyze as many data points as possible.
Even when an ID verification is successful at either flagging or verifying a guest, it still can’t determine their intentions at your property. To do this, you need to assess the booking parameters. By examining details on and surrounding the guest’s reservation, you can get a better idea of who they are and what they’re planning to do during their stay. For example, there are certain booking conditions that might make a reservation higher risk, including:
- One-night stays
- Last-minute bookings
- Local guests
If a reservation is booked under these conditions, that doesn’t mean that it’s inherently risky. However, you should look at these risks in comparison with other data points.
There are data points connected to a guest’s reservation that can let you know whether or not they’re involved in suspicious or malicious activity. By analyzing the guest’s digital footprint, including their email address, phone number, IP address and social media presence, you can confirm they are who they say they are—or confirm any suspicions you had concerning their “story” (their purpose of stay, who they’re traveling with, etc.)
While ID verification is essential to your business, it’s just a piece of the puzzle. To properly determine the risk level of a reservation, you need to analyze the guest’s entire profile. That means looking at all data connected to the guest, their booking and their digital footprint.